Table of Contents
SUMMARY
Cyber Crime is a stage through which the residents of India can report digital wrongdoing perpetrated against them on the web. We are living in the cyber age. This means we are surrounded all around by digital devices, computers, and Information technology. Cyber security is a security that is provided against cyber crimes. They are used to protect from malicious attacks. Several techniques are used for cyber security depending on the types of cybercrimes. Some cyber cells are usually done and some of the cyber security techniques are discussed below.

WHAT IS Cyber Crime
Those crimes take place through the means of the Internet when someone commits illegal activities on the use of the Internet. These can be termed cyber crimes. Those crimes include harassment, stealing privacy or personal data, banking fraud, stealing identities, and hacking.

In 1999 fifteen-year-old hacker Jonathan James from Florida committed a cyber crime by hacking NASA computers it was a three-week system shut down.

INTRODUCTION
In modern times, Internet has become the most useful thing. Everyone uses it. And it is true that our lives are incomplete without the use of the Internet. Everyone has the Internet at their fingertips if we are using any social media account, using Google Maps, withdrawing our money through online banking or we are doing online shopping or we are chatting with our friends. In every field, Internet has become a basic need of life and we will become useless without the Internet.
For all these purposes we need to give our personal information and data to companies and websites. Even when we are using social media accounts or when we are downloading any app to the play store, we agreed to their privacy policies. After then they caught a command over our whole information, pictures, our location, and they got a command on our cameras also, and also on our audios. They are listening to us.

They are using our personal information and data. Now the security of our data is very important. We should have the guarantee that our money placed in banks is safe or not.
HOW CAN WE SAVE OUR DEVICES FROM CYBER CRIME?
Cyber security is providing security over all electronic devices, Internet, and information technology over all these cyber crimes and malicious attacks.
IT experts provide cyber security to our data information.
All the major fields Including Air Force, military, financial, government, educational, and medical fields require us to save our data and information. The security of this data is very important from every perspective that’s why cyber security is very important.
Cyber security is a whole department working at a greater level. In order to save our devices, we can adopt some techniques of cyber security. Or we can take help from the cyber security department.

TECHNIQUES OF CYBER SECURITY.
Some techniques are involved in cyber security which helps to provide protection against malicious attacks.
These techniques depend on which kind of data we are connected to and which type of cyber attack we are prone to.
MOST COMMON TYPES OF CYBER ATTACKS
MALWARE ATTACK
Its other name is malicious software. This means that software which can harm your system. It can enter your system through different sources. One of the major sources is the Internet. Like while you are downloading something, visiting any movie website, when you click on an advertisement, or when you use some CD DVD, or USB from an unknown source.

Virus, Trojan, and worms are its three types
VIRUS
It can corrupt any file or any particular software.

WORMS
They spread quickly like worms they make different files of the same copies and spread from computer to computer.

TROJAN

It attacks in form of software. They enter our system, and they can Block your computer and open doors for other viruses.
PHISHING ATTACK.
These types of attacks are sent through email, and they ask users to click on the link and enter personal data most of the financial institution’s attacks are done by a Phishing attack.
They usually send these emails to steal data like credit cards information or other sensitive data.

MAN IN THE MIDDLE ATTACK.
This commonly happens when the Wi-Fi system is unsecured which means that the attacker is eavesdropping on the communication between two parties. The attacker can also change the communication. It also happens when the end-to-end encryption system is not as strong. It can also happen during our WhatsApp chats. Sometimes when we open a chat there is written end-to-end encrypted. This is what it means. It is also known as MITM attacks we can avoid these types of attacks by avoiding public or insecure Wi-Fi connections. Especially while using banking websites, we should be careful.
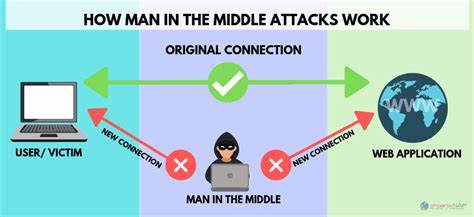
HOW TO DISCLOSE MITM ATTACK.
By seeing the URL in the address bar. Usually, the lack of S in HTTPS is a sign of an MITM attack, and if your connection is frequently connecting and disconnecting. It can also be a sign of a MITM attack.
PASSWORD ATTACKS.
These types of attacks can be done by guessing the passwords. They can also use such types of software which can crack or guess passwords.
SOME OF THE TECHNIQUES FOR CYBER SECURITY ARE.
There are multiple jobs in cybersecurity. Professionals are hired to identify cyber threats and provide security to them.
Some of the techniques are:
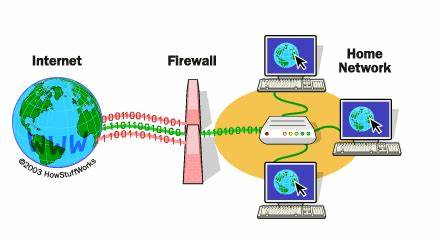
FIREWALL.
Installing firewall. It worked as a wall between a computer and the Internet all data which is coming through Internet will reach your device after filtering through a firewall. They will work as a safeguard for your system.
ANTIVIRUS SOFTWARE.
For malware attacks, there should be antivirus software present on your device, and it should be updated. Antivirus software should be taken from the trusted authority. And otherwise, we can also get attacked in form of Trojan.

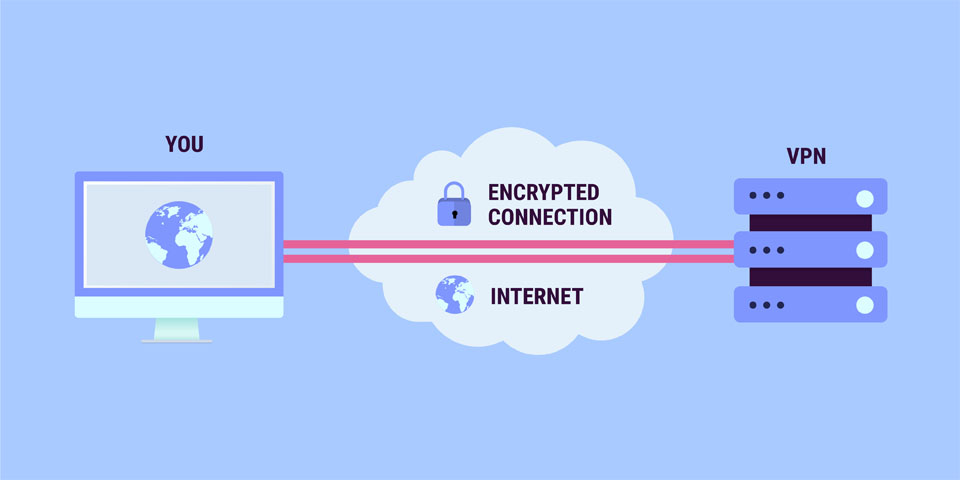
VPN
VIRTUAL PRIVATE NETWORK
Everything which we are doing on the Internet is assigned to an address. Through IP address we are using the Internet. The request is first sent to the server and then it is accepted. The Internet service providers can also track our every step throw this IP address.
Open Wi-Fi networks can be very harmful because any hacker can hack or trace your device through an IP address.
So, with the use of a VPN the connection between you and your server will be completely encrypted, no one can trace your request. You can use all the contents securely and can visit any blocked website also.
HONEYPOTS
They are dummy computer systems that are used to attract hackers just as honey attracts flowers. They are mostly used by large companies involved in cyber security research.
It attracts the hacker and then tracks all the activities of hackers.
They are working as undercover agents like police officers. To catch the hackers and track their activities.

There are two types of honeypots.
PRODUCTION HONEYPOTS.
They are used to capture limited information from hackers.
RESEARCH HONEYPOTS.
They are generally used by research military and government organizations. They capture extensive information. They are complex to maintain.
CONCLUSION:
Cyber security is a very important factor in every field of work. Including the Medical field, government field, and air traffic controller. Hackers and cyber criminals have become too strong, and they are around us. so, protection against it also has to be strong. Protection for hardware and software both are important.